Writeups for Alpine 1,2 & Truth and Falsehood from BYU CTF 2022

Writeups for some of the challenges i solved from BYU CTF 2022
Published on June 01, 2022 by 0xRar
Writeups CTF Forensics Cryptography
4 min READ
This ctf was organized by the Cybersecurity Student Association its your basic 2day ish ctf with a ton of amazing well made challenges, in this ctf i played with my new team b3R4bb1t$ and we were placed 5th out of 435 teams.

Alpine 1:
Description:
In this challenge you need to find the file and its path that is giving access to the attacker. The system administrator (root:strongpassword) created a user for a local user, Matt Johnson (mjohnson:hardpassword). An attacker was able to brute force Matt’s password and login. The system administrator changed Matt’s password (mjohnson:secretpassword), however the attacker is still able to SSH into the machine.
Provide the path and file name that is allowing the attacker to still have access (persistence): byuctf{/full/path/to/file}.
Alpine is a 3 challenges linux forensics series though i only solved 2 of them, the whole idea is an attacker have hacked the system and we have to investigate the virtual box machine(.ova) and find more information about what the attacker did on the system.
Solution:
Alpine 1 is an easy forensics challenge, we need to log in into the vm and find the file that gives the attacker an access, we are given 2 accounts i went ahead and logged in using the root account, clearly by the challenge description the attacker now have a persistence access to the machine so first thing i did was head to /home/mjohnson and wrote ls -la to list all the files and found some stuff that can lead us the right way or even solve the whole challenge
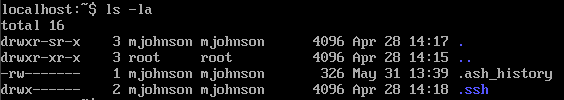
so i decided to check the .ash_history for commands made by the attacker
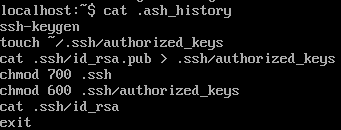
great thats the file giving the attacker access /home/mjohnson/.ssh/authorized_keys
Flag: byuctf{/home/mjohnson/.ssh/authorized_keys}
Alpine 2:
Description:
What was the IP address of the attacker? (Note: Matt Johnson never logged in remotely.)
Flag format - byuctf{ip_address}
Solution:
Alpine 2 is a medium difficulty forensics challenge, same as alpine 1 we have to investigate the same system and answer some questions about the attacker’s doing, this time we need to find the ip of the attacker, and as we seen on the first challenge the attacker has persistence access (ssh) to the machine so i decided to check the /var/log/ which is the directory that keeps logs in a linux system inside of it i found multiple files or logs
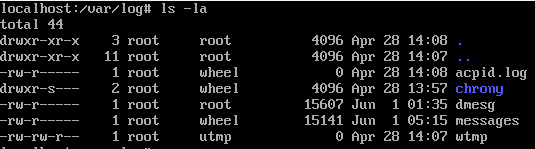
as we can see not all logs contain data, but the messages file is the most interesting one which contain a variety of messages, such as mail, kern, and ofcourse auth which will give us login attempts via ssh, and remember Matt Johnson never logged in remotely, so i went ahead and grep’d ssh
cat messages | grep ssh
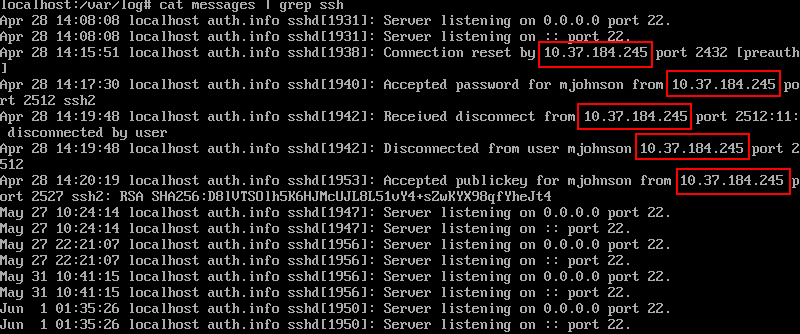
which gave us some ssh activities with the remote ip address of the attacker
Flag: byuctf{10.37.184.245}
Truth and Falsehood:
Description:
Someone tried to send me the flag, but I think I missed a few characters, because most of this doesn’t make sense.
The flag should be in byuctf{[a-zA-Z0-9_]*} format, but I don’t see it there.
Solution:
Truth and Falsehood is a medium cryptography challenge, nothing special about this challenge but from the first look at the challenge we are given a really long base64 of a really long text you won’t find anything just by decoding because there is alot of words missing of the base64 so i pasted the string in cyberchef and started deleting a lot of the base64 until i got the flag !

i can see a lot of teams struggled with this one because it was so random and it had something to do with base64 not having an error corrections? and it helped us a lot with points just because only 40 teams solved it and we got first blood on the challenge.
Flag:byuctf{base64_has_no_error_corrections_a5EdFabe}
Thank You For Reading ♥